Authentication Methods Via Dex
This page describes how to setup and configure other forms of authentication via Dex.
Useful Definitions
Authentication - Authentication is the process of verifying the identity of a user.
Authorization - Authorization is the process of determining if an identified user has access to a particular resource or not.
Connectors - When a user logs in through Dex, the user’s identity is usually stored in another user-management system: a LDAP directory, a GitHub org, etc. Dex acts as a shim between a client app and the upstream identity provider. A connector is a strategy used by Dex for authenticating a user against another identity provider. Dex implements connectors that target specific platforms such as GitHub, LinkedIn, and Microsoft as well as established protocols like LDAP and SAML.
Dex - Dex is an identity service that uses OpenID Connect to drive authentication for other apps. Dex acts as a portal to other identity providers through connectors (see previous definition). This lets Dex defer authentication to LDAP servers, SAML providers, or established identity providers like GitHub, Google, and Active Directory. Clients write their authentication logic once to talk to Dex, then Dex handles the protocols for a given backend. For more information about Dex, click here.
LDAP/AD Auth Protocol - Lightweight Directory Access Protocol (LDAP) is an open and cross-platform application protocol for directory services authentication. Directory services, such as Active Directory (AD), store user information, account information, and security information like passwords. The service then allows the information to be shared with other devices on the network.
OIDC Auth Protocol - OpenID Connect (OIDC) is an authentication protocol based on the OAuth2 protocol (which is used for authorization). OIDC uses the standardized message flows from OAuth2 to provide identity services. It allows clients to confirm an end user's identity using authentication by an authorization server.
T4K Auth Support - T4K supports authentication via KubeConfig files and via Dex, which is an identity service IDP plugin that uses OpenID Connect to drive authentication for multiple applications, by deferring authentication to other identity providers like LDAP.
Introduction
Trilio For Kubernetes (T4K) uses Dex as a portal to other identity providers through connectors. For more information about these services, refer to the Useful References section at the top of this page.
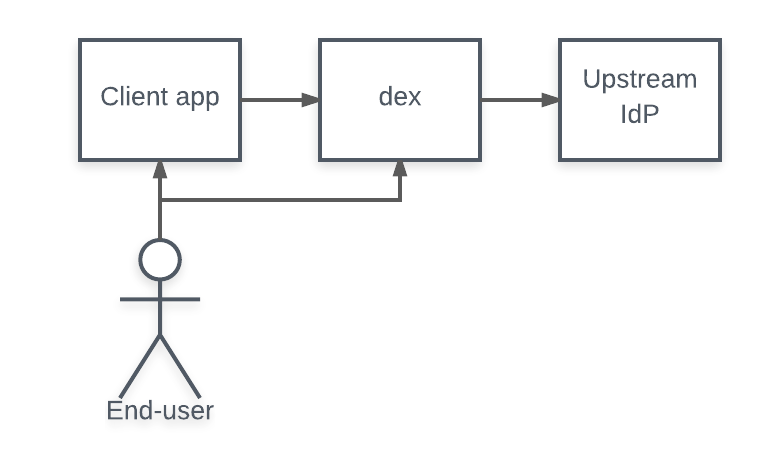
A connector is a strategy used by Dex for authenticating a user against another identity provider. Dex implements connectors that target specific platforms such as GitHub, LinkedIn, and Microsoft as well as established protocols like LDAP.
Pre-Requisites
LDAP / AD: LDAP protocol requires one read-only user who can perform LDAP searches to fetch users and groups.
OpenShift: By default, OpenShift clusters already have Login Via OpenShift configured during the Trilio installation. T4K does not require any additional user input for that.
Configuration
STEP 1: Configure your OIDC authentication provider to allow authentication for T4K Web. Create a new application on the authentication provider portal, then use the T4K callback URL http(s):///dex/callback in the OIDC provider portal, and finally, generate client and secret keys.
The following are links to achieve this for the most popular OIDC authentication providers:
Navigate to the Google application's API Credentials page.
Click + Create Credentials.
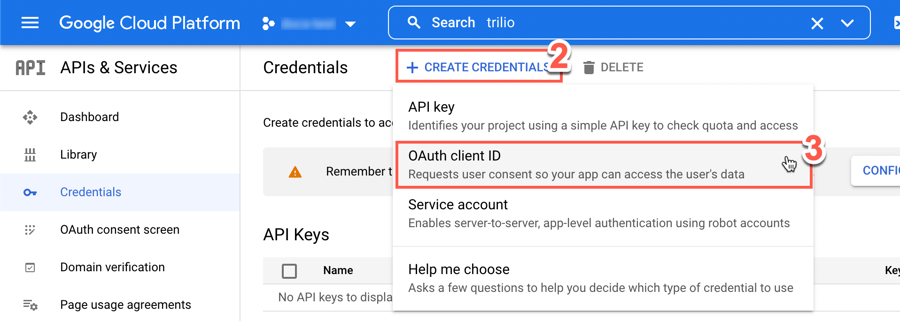
From the dropdown displayed, click OAuth client ID.
In the Application type field, use the dropdown menu to select Web application.
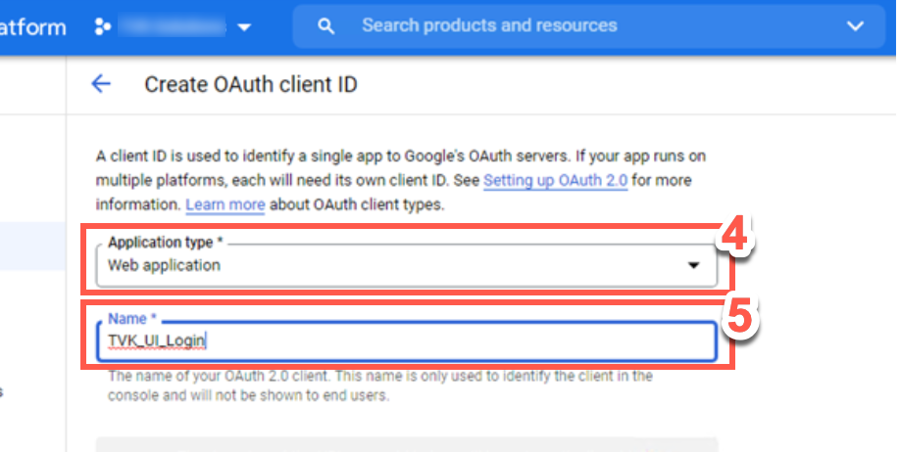
Type a meaningful Name for the OAuth ID.
Add authorized redirect URIs as the TVK call back URL. For example, for the NodePort use http://default.k8s-tvk.com:32663/dex/callback and for the LoadBalancer use: http://gke-270.k8s-tvk.demo.trilio.io/dex/callback
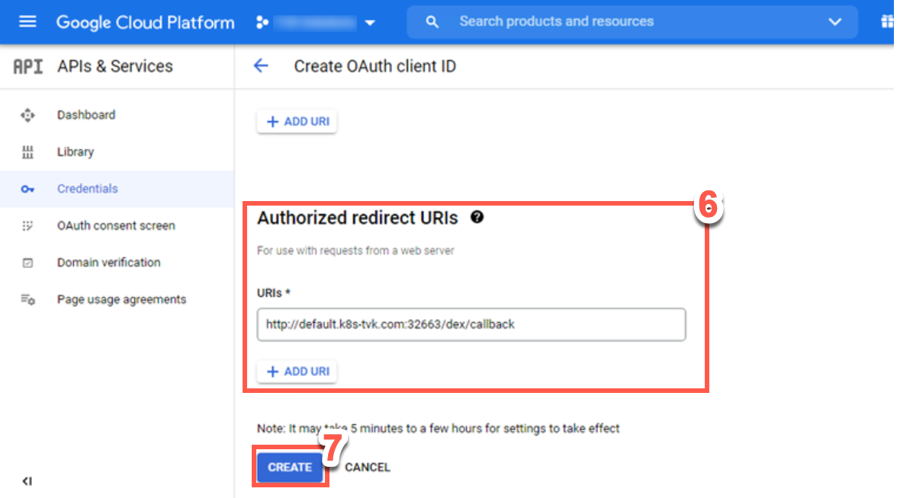
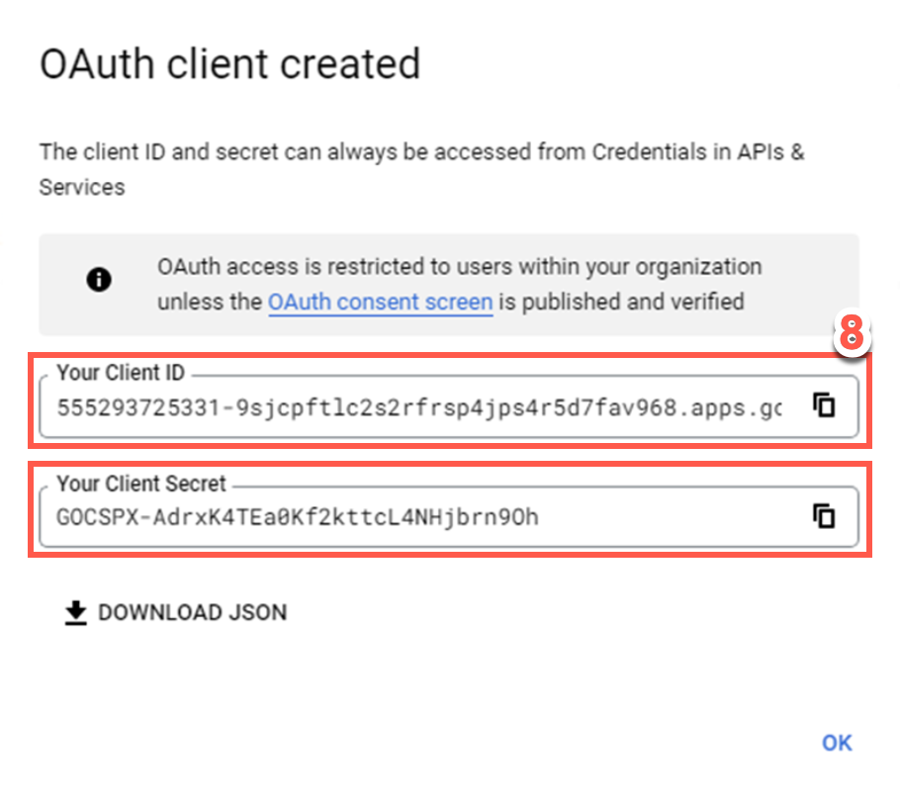
Click Create.
Copy Your Client ID and Your Client Secret values displayed.
Navigate to the GitHub application: https://github.com/settings/applications/new
Create a new application on the authentication provider portal, then use the TVK callback URL http(s):///dex/callback in the OIDC provider portal, and finally, generate client and secret keys.
Navigate to the LinkedIn application: https://developer.linkedin.com/
Create a new application on the authentication provider portal, then use the TVK callback URL http(s):///dex/callback in the OIDC provider portal, and finally, generate client and secret keys.
Navigate to the GitLab application: https://gitlab.com/-/profile/applications
Create a new application on the authentication provider portal, then use the TVK callback URL http(s):///dex/callback in the OIDC provider portal, and finally, generate client and secret keys.
Ensure that the LDAP server is deployed and configured.
Retrieve the following details from the LDAP server, as these are used in the next steps:
LDAP server host IP or FQDN e.g. ldap.tvkdemo.org
DNS domain name e.g. tvkdemo.org
bindDN: cn=username,dc=tvkdemo,dc=org
bindPW: password
Navigate to the Azure Home > App registrations > Register an application:(https://portal.azure.com/#blade/Microsoft_AAD_RegisteredApps/ApplicationsListBlade)
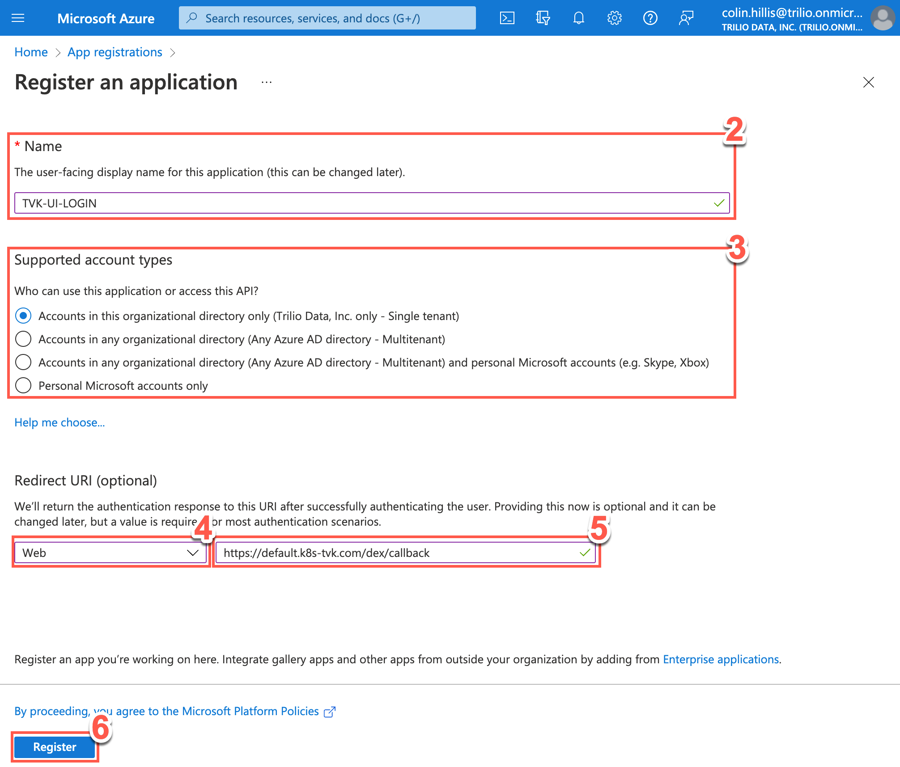
Type a meaningful name for application; i.e. TVK-UI-LOGIN.
From the radio button options, choose who can use this application or access this API.
Select Web from the dropdown menu.
Type the redirect URI https://default.k8s-tvk.com/dex/callback.
Click Register.
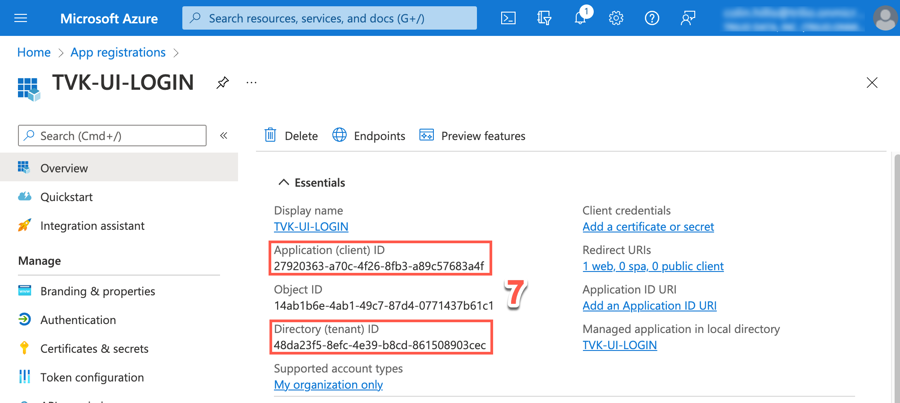
Note down the following two details:
Application (client) ID, e.g.
27920363-a70c-4f26-8fb3-a89c57683a4fToken endpoint - https://login.microsoftonline.com/48da23f5-8efc-4e39-b8cd-861508903cec
In Azure's left menu panel, select Certificates & Secrets.
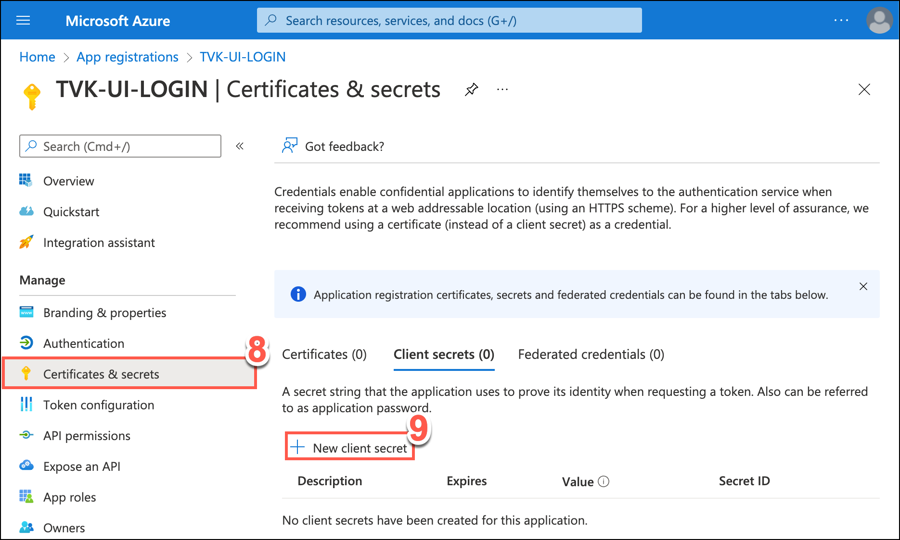
On the screen displayed, select + New client secret.
In the pop-up window displayed, type a meaningful Description for your client secret, e.g. TVK UI Login Secret. Also set an expiry period.
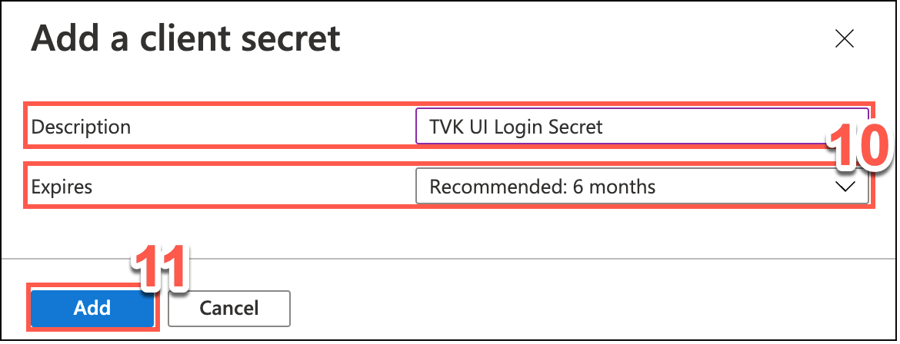
Click Add.
The Client secrets tab automatically displays available secrets. Copy the Value for the secret just added.
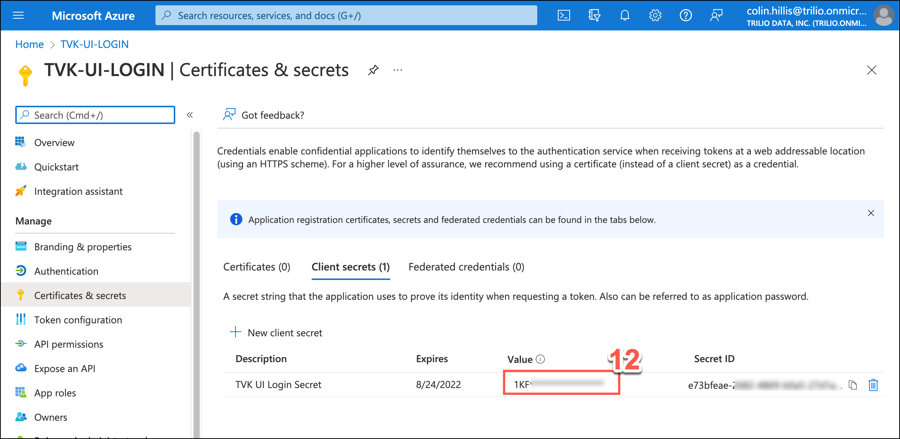
Using the copied value from the previous step, configure the TVK Management Console access over HTTPS. Refer to the following documentation guide: Here
By default, OpenShift clusters already have Login Via OpenShift configured during the Triliovault installation. TVK does not require any additional user input for that, so Step 1 can be skipped for OpenShift.
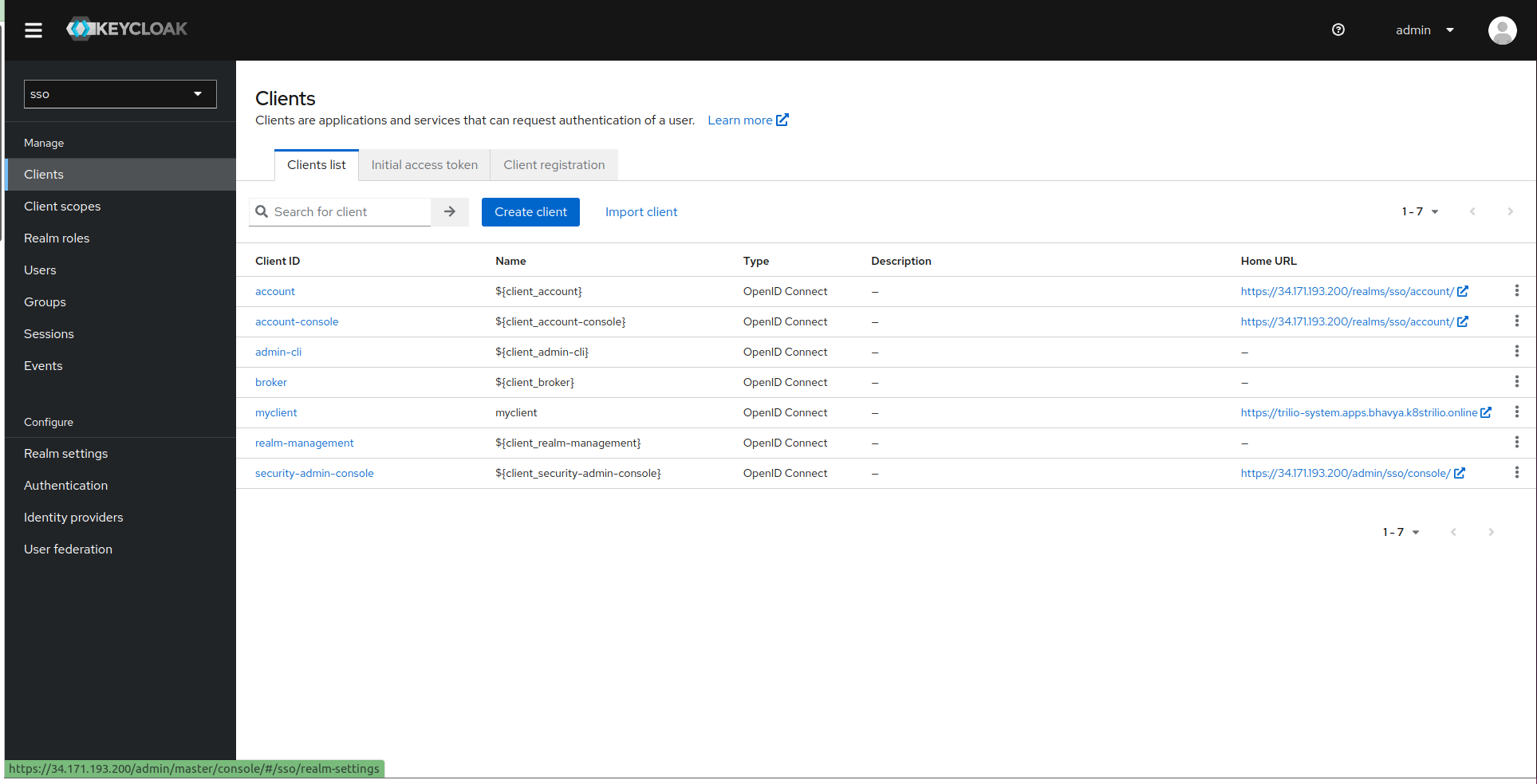
Login into Keycloak Management portal.
Select the realm which use for authentication.
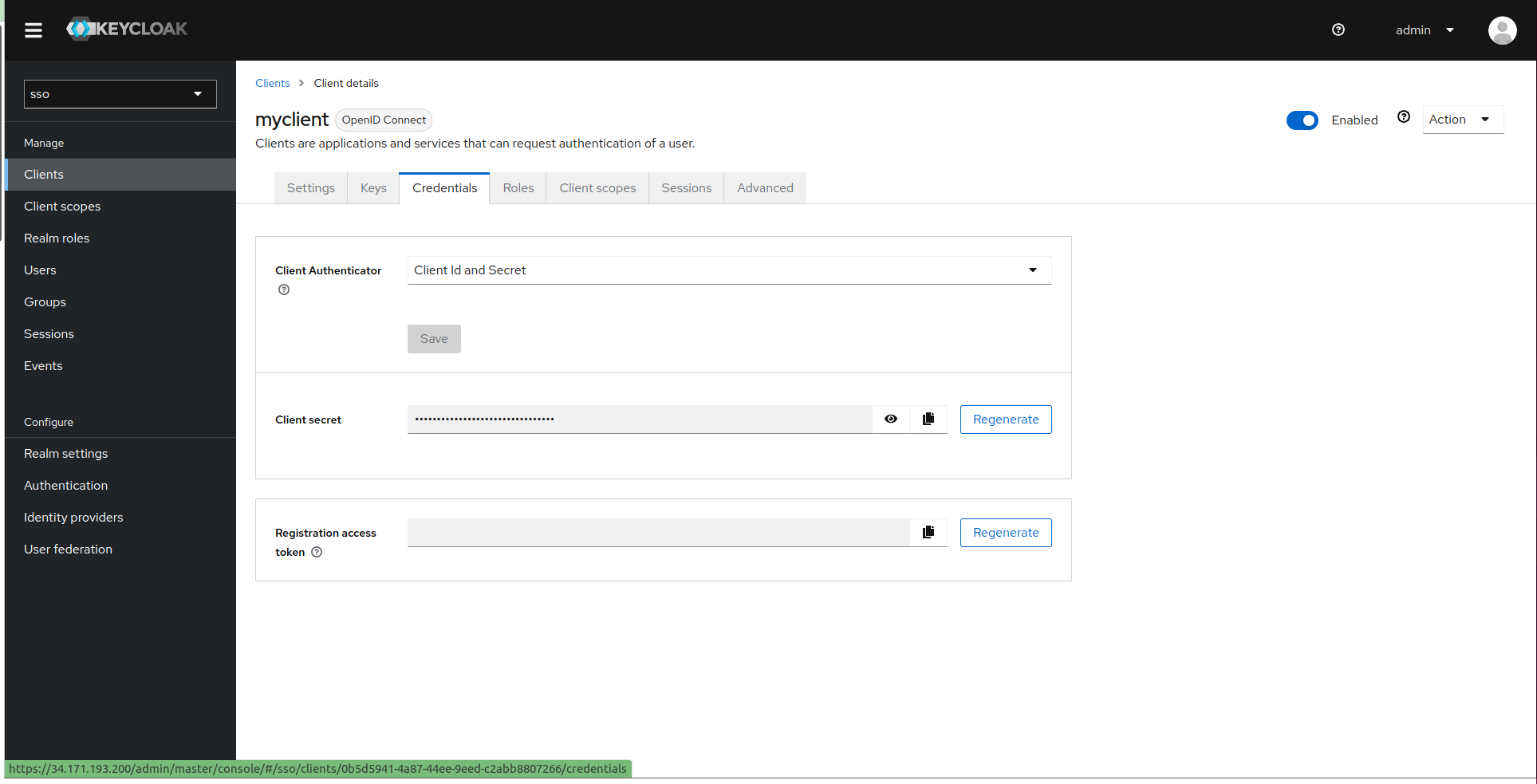
Navigate to the Client Tab and copy Client name for ClientID
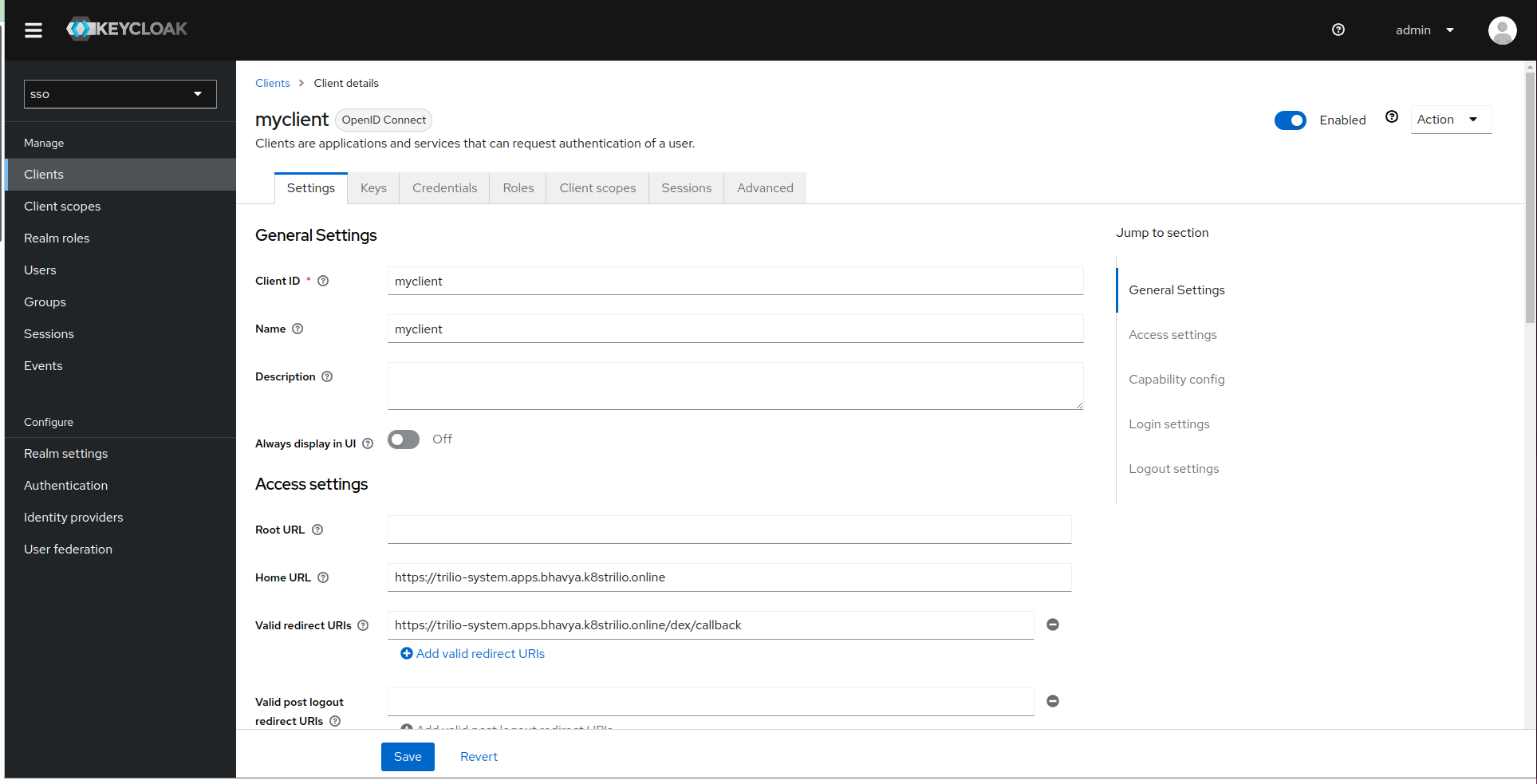
Select the client and configure it with TVK URL and callback URL https://<TVK_URL>/dex/callback.
5. Go to Credential tab and Copy Your Client Secret values displayed.
Step 2: Prepare a secret.yaml file with the name triliovault-dex that has all the copied details of the authentication provider from Step 1 (Your Client ID and Your Client Secret). Refer to the relevant tab below to guide you how to form your secret.yaml for each of the main providers.
You can choose other authentication providers and you can determine what details should be included in the associated secret.yaml file by reviewing the most common options below.
The following is a more detailed example with LDAP on SSL with multiple groups:
Refer this doc for all other configuration details of all other connectors and any customer configurations required.
Step 3 (Optional) - Only if using 'Port Forwarding' or 'NodePort', update your secret.yaml file created in Step 1 with an additional key T4K_URL. This provides your custom URL with a port to access the T4K dashboard.
Insert a new line in the secret.yaml file immediately after code line 9 (applies to all examples given in Step 1) and insert the following:
TVK_URL: http://<ingress-domain>:1234Save the secret YAML file using the same name as before.
Step 4: Apply the new secret.yaml in the namespace of the k8s cluster where T4K is installed.
This causes the creation of the T4K Dex deployment, which will reflect changes on the T4K Management Console UI. You will now find another way of logging in, according to what you have just configured, i.e. Login Via Github.
Step 5: Create a cluster role binding using the below command, making sure to replace the user with your user/email ID and the clusterrolebinding name, since it must be unique:
Step 6: Navigate to the Management Console UI login page. You will now see an additional login method, which corresponds to what you have just configured in the previous steps; e.g. Login Via Github.
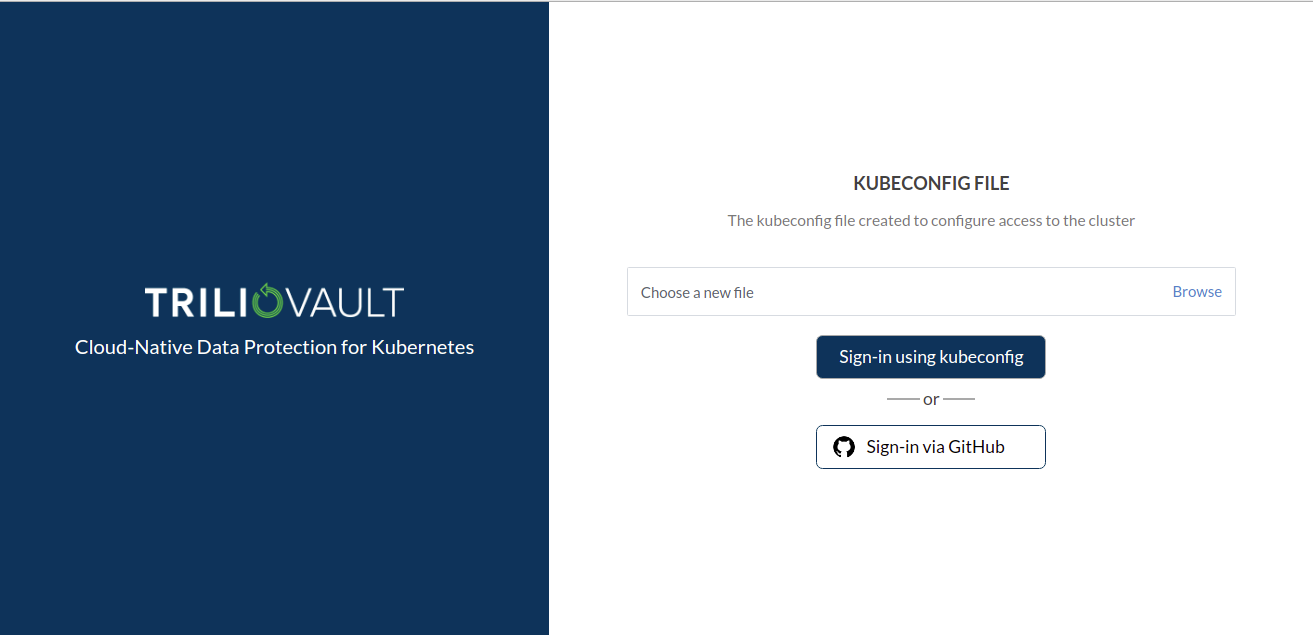
For LDAP, you will be prompted for your Username and Password.
Last updated